RAYMOND OGLESBY @RaymondOglesby2
September 2, 2025 – 8 minutes read time
Note! Although we recommend you use this tip, we are NOT responsible for what happens to your data. Also, remember there is no such thing as “privacy” on the web. If major USA companies get hacked, so will you. But this tip will help protect your data.
Overview
National Public Data is back with new owners, joining the ranks of other creepy, people-finding services. The website, infamous for its role in leaking millions of Social Security numbers in 2024, has returned with the ability to look up anyone’s personal information.
The site shut down in December amid a wave of lawsuits against parent company Jericho Pictures after a breach exposed an estimated 272 million unique SSNs and 600 million phone numbers. Since then, the site has been relatively dormant. But recently, we spotted it springing back to life with a new interface.
It looks like the domain has changed hands:. In a page about last year’s breach, the site’s new owners write: “Important Notice: Jericho Pictures, Inc., the Florida company that suffered a major data breach in 2024, no longer operates this site. We have zero affiliation with them. We are keeping this page, originally posted by Jericho Pictures, Inc., intact so its history remains traceable.”
Why You Will Like This Tip
- Protect your privacy from others or companies
- View and/or remove your personal data from pubic searches
- Be in control of your data
System Requirements
This tip was performed on a Dell XPS desktop running Windows 11 Pro. Screenshots are from the latest update for the Google Chrome browser.
Your Profile On National Public Data Website
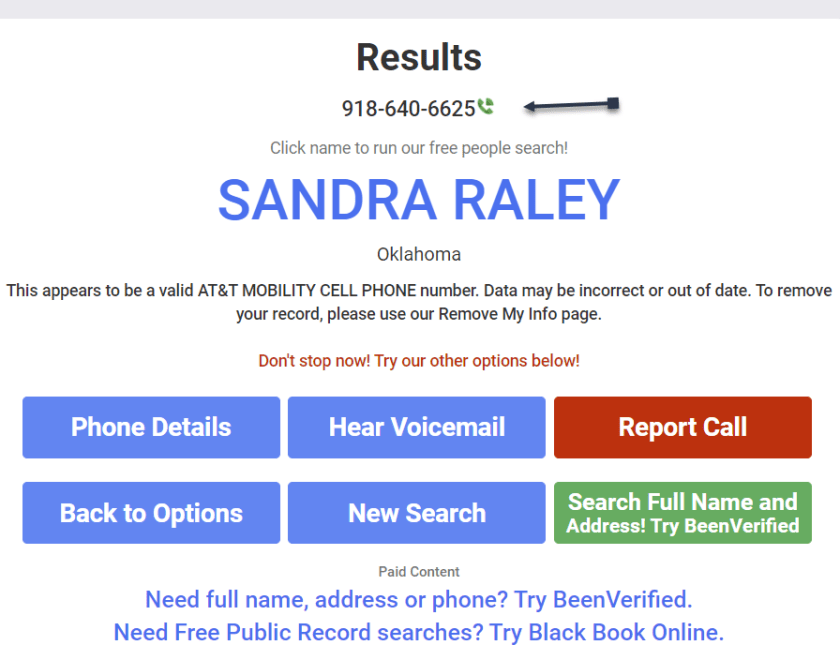
First, it’s relatively easy to look up anybody’s information using their website. Click here to access their interface. Refer to the image below:
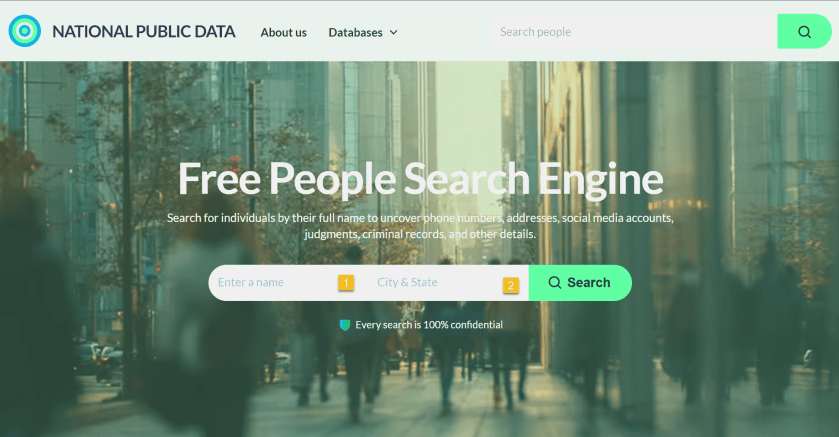
The site does not explain who the new owners are, but a domain lookup shows that it’s registered to Florida-based “Perfect Privacy,” (what an oxymoron), a brand name associated with a VPN service. However, Perfect Privacy VPN has no affiliation with National Public Data.
The new site functions as a “free people search engine,” which might alarm the public since National Public Data housed a huge trove of sensitive data on Americans.
It is unclear where the site is getting its data. But the new National Public Data says: “We collect the data you find on our people search engine from publicly available sources, including federal, state, and local government agencies, social media pages, property ownership databases, and other reliable platforms. After the data is in our hands, we verify and filter it to make sure it is indeed accurate and up-to-date.”
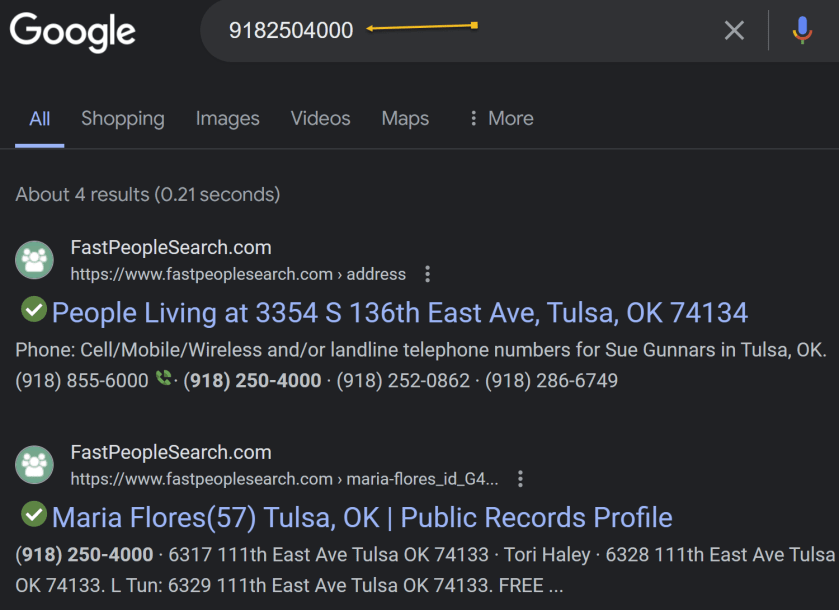
Next, key in your full name, City/State. Both fields are autofill. As you enter the information, it pops up with matching criteria. Then tap the Search button. The search is extremely FAST. I tried both of my names and got the same results.
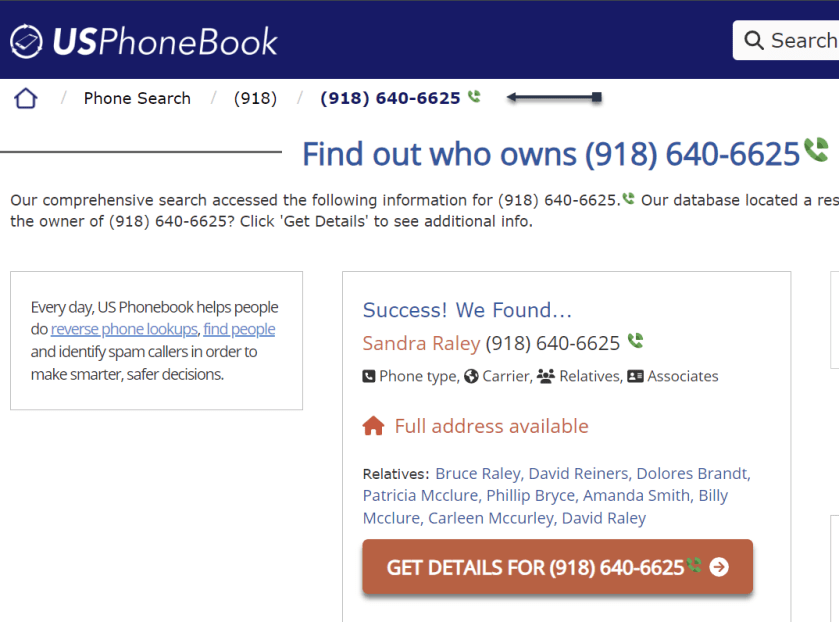
My wife used the site in her genealogy research to find a distant cousin’s phone number and contacted him. See the image below:
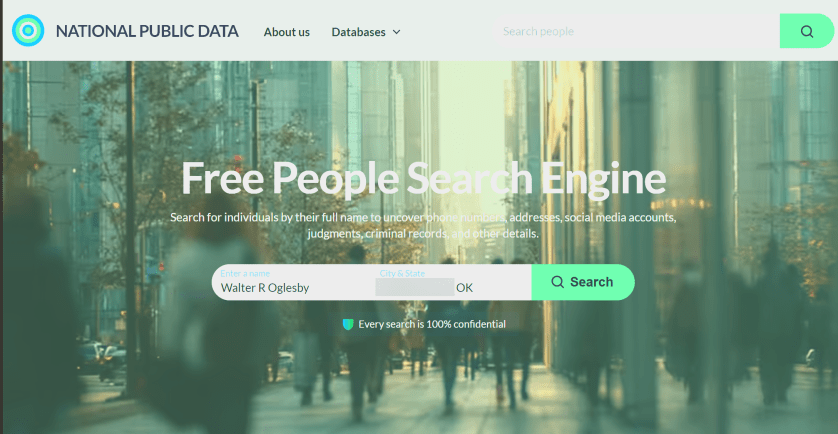
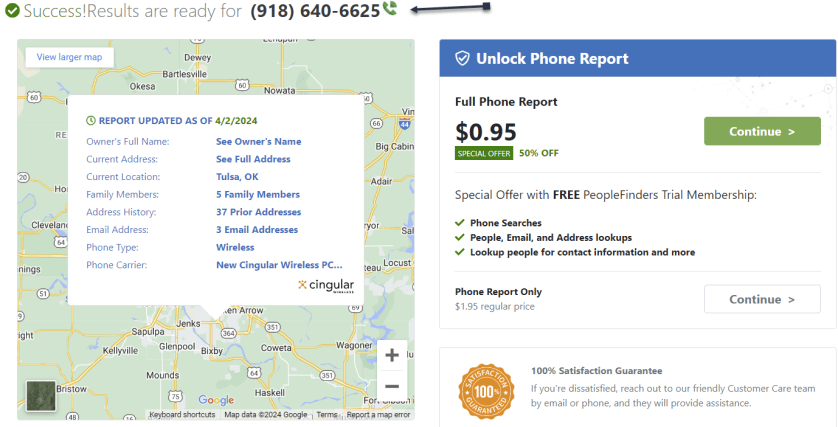
Now, your basic profile information will be displayed. We have redacted specific fields for privacy. We noted that the basic profile information was correct except for the landline phone number, which we no longer have. When I clicked on my relatives, the data was incorrect. To view more information, click the View Full Profile button. See the following image for basic details about myself:
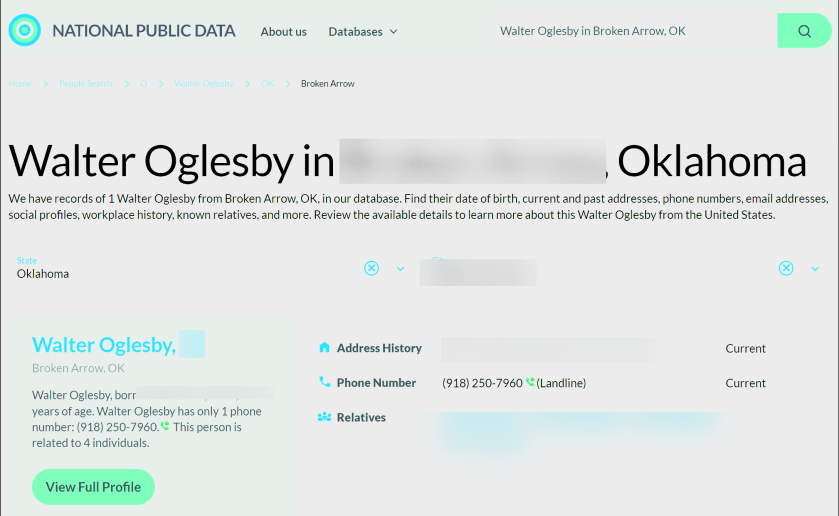
Still, what makes the site disturbing is how you can freely look up people’s data, including neighbors, and sometimes find accurate addresses, phone numbers, and dates of birth, along with a person’s relatives. None of the data is behind a paywall. That said, the new site is not much different from other people-finding services, which serve up similar data for free.
The new National Public Data adds: “On our people search website, you can find pretty much anything you need, from someone’s contact info, location, age, and birthday to workplace, relatives, and criminal records. No need to sift through different web pages.” It does not reveal your SSN.
Next, the data it reveals is a lot. Refer to the image below about the data it finds:

Opt-Out From National Piblic Data Site
Now, the new National Public Data site has an opt-out form to delete your profile data. However, many users are likely unaware of such an option, enabling these types of sites to continue trafficking their information. See the image below:
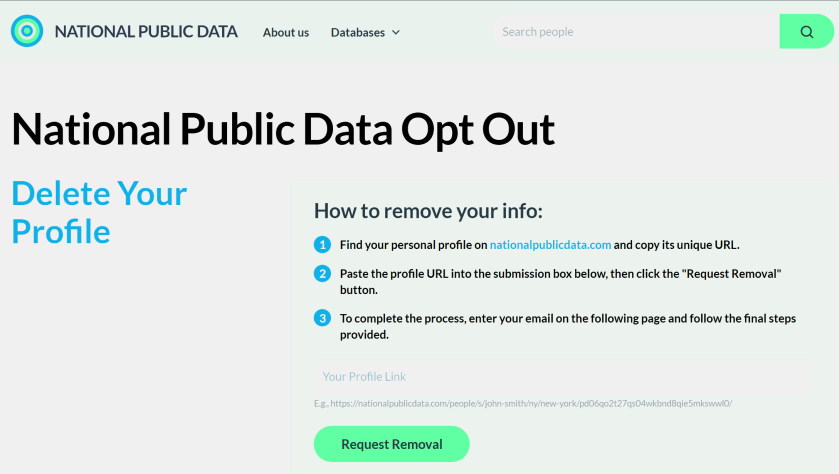
Remember, proactively managing your online privacy and staying informed about potential data breaches are crucial steps in protecting your personal information.
Here’s how to delete your data:
- Search your name on nationalpublicdata.com
- When you find your profile, click View Full Profile
- Copy that URL
- Go to nationalpublicdata.com/optout.html
- Drop the URL into the Your Profile Link field and click Request Removal
- Enter an email address, and the site will send you a message and ask you to click to confirm deletion. You need a separate email address for each profile you want to delete.
We tried the opt-out function, and the site appears to remove our data immediately. Some commenters say they have not received the confirmation email. Check your Spam folder and make sure you are dropping the full URL for your profile into the Link box, not just the search results page.
Atlas Privacy Website
Sites such as Atlas Privacy have emerged to help people remove their data from the open web and people-finding services. Note: we did not try their service.
Atlas Privacy focuses on removing your personal information from data broker websites and other online sources, NOT your own website. They help you regain control of your data by removing it from places where it’s being collected and shared without your consent.
They scan over 150 sites to remove your information and help protect your privacy by removing your name, age, address, phone number, and other personal details from these sources. Atlas Privacy does not have its own list of websites it searches, but rather, it targets specific data brokers and people finder sites.
Unlike the National Public Data, you must create an account to use their service. There are both free and paid services.
After you have removed your data, recheck to see if it’s actually deleted!
Note! Remember you are responsible for your own data. Acting proactivity by removing your data allows you to be in control.
Want to Recover Your Dara (Why Would You)
National Public Data
If your data has been removed from Natural Public Data sources, it is generally not possible to get it back in the same way it was stored. Once data is deleted, it is often permanently removed from the system or archived in a way that is not easily accessible. However, the possibility of data restoration depends on the specific circumstances of the removal and d the policies of the data provider.
Atlas Privacy
If your data has been removed from Atlas Privacy, in some cases, you may be able to restore data that has been removed.
Sources: National Public Data, Perfect Privacy, Jericho pictures, Microsoft, PCMag, Atlas Prvacy, Meta
Disclaimer
Technology is constantly evolving, and smartphone and desktop tech rarely remains static. Therefore, the information in this post is only accurate as of the date it was written. Blog posts that are older than six months may contain instructions that are no longer compatible with your device or operating system. We hope that the content from previous posts continues to function as intended. Thank you for reading TechSavvy.Life, where technology works for you.
Quote For the Day
“The art challenges the technology, and the technology inspires the art.”
– John Lasseter, Co-founder of Pixar
(X) Twitter Info
That’s it. Please feel free to share this post! One way to share is via Twitter.
Just click the Tweet icon below. This will launch Twitter where you click its icon to post the Tweet.
Checkout TechSavvy.Life for blog posts on smartphones, PCs, and Macs! You may email us at contact@techsavvy.life for comments or questions.
Tweet
I Would Like to Hear From You
We value your feedback! Was this post helpful? Please share your comments with us. If you have a tech question related to your computer or smart device, feel free to reach out. Just send an email to contact@techsavvy.life, and be sure to include the device, app, and version you are using. To assist us further, you can also attach screenshots related to your inquiry.
The author’s Vietnam eBook on the “Battle for Tra Bong Vietnam: Events and Aftermath” can be accessed from a Kindle device or the Kindle App for a desktop or smartphone. The apps are free.