Insert dRAYMOND OGLESBY @RaymondOglesby2
April 1, 2025 – 6 minutes read time
Overview
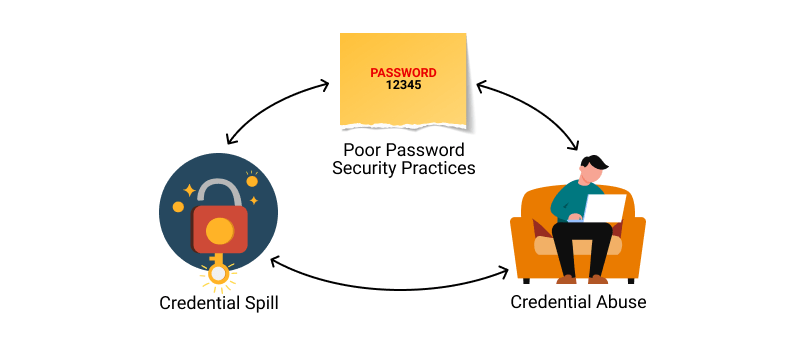
Recently. Apple took the unusual step of turning off its highest level of iCloud encryption, Advanced Data Protection (ADP) for customers in the UK. The British government has reportedly demanded that Apple provide a method for law enforcement to access encrypted data as part of criminal investigations. But that creates a serious security problem, because this type of backdoor access can also be exploited by criminals or untrustworthy governments.
Why You Will like This Tip
- Have the best encryption for your Apple devices.
- Prevent hackers from accessing and viewing your data.
System Requirements
See below for the Apple software versions. These screenshots were captured using iOS 18.3.2 on iPhone 14 Pro.
Click here to learn how to update your iPhone to the latest iOS version.
United Kingdom vs United States
For people in the UK, ADP can no longer be enabled. If you are currently using ADP, you will need to turn off the feature at a future date.
If you are outside the UK and concerned about who can see your data, ADP adds an extra layer of security by making it unreadable even by Apple. If ADP is disabled, your data could be at risk because it can still be unlocked by Apple, a legal request or a data breach.
Let’s explore how to turn Advanced Data Protection on, and how it differs from the default iCloud encryption methods.
How Does ADP Work
The key difference between ADP and how Apple encrypts data by default is how accessible your information is when stored on Apple’s servers.
In what Apple calls standard data protection, information sent between points, such as files stored on iCloud Drive and iCloud backups of your devices, is encrypted and transmitted securely. If someone intercepts that data between the two points, they will see only gibberish.
That data remains encrypted when it’s stored on Apple’s servers, so you can access it from other devices, for instance. However, Apple can still access the encryption keys to unscramble and read the data; and provide it to law enforcement following a legal request.
By contrast, when you enable Advanced Data Protection for iCloud, the data is end-to-end encrypted, meaning only your trusted devices possess the encryption keys to read it. The information remains encrypted on the servers, and not even Apple can access its contents. (Not all iCloud data can be end-to-end encrypted. Apple breaks out-which types of information, such as iCloud Mail messages, that remain covered by standard data protection even when ADP is turned on.)
The UK’s Investigatory Powers Act, the “Snooperd’s Charter”, makes that inaccessibility illegal, which is why Apple is turning the feature off for UK customers.
Some services are end-to-end encrypted regardless due to the sensitivity of the data, such as passwords, information stored in the Health app and payment information.
Setup Your Account for ADP
Note! Setting up ADP applies to all devices in your Apple account.
To set up ADP on your account, first make sure you have met all the prerequisites for the feature:
- Your Apple Account must use two-factor authentication.
- You must have a recovery method set up in case you lose access to your account. That can be a 28-character Recovery Key or a person you have designated as a Trusted Contact.
- Every device connected with your Apple Account must be able to run at least
- iOS 16.2, iPadOS 16.2, MacOS 13.1
- WatchOS 9.2
- TVOS 16.2
- HomePod 16.0
- For Windows computers, make sure iCloud for Windows is at version 14.1 or later.
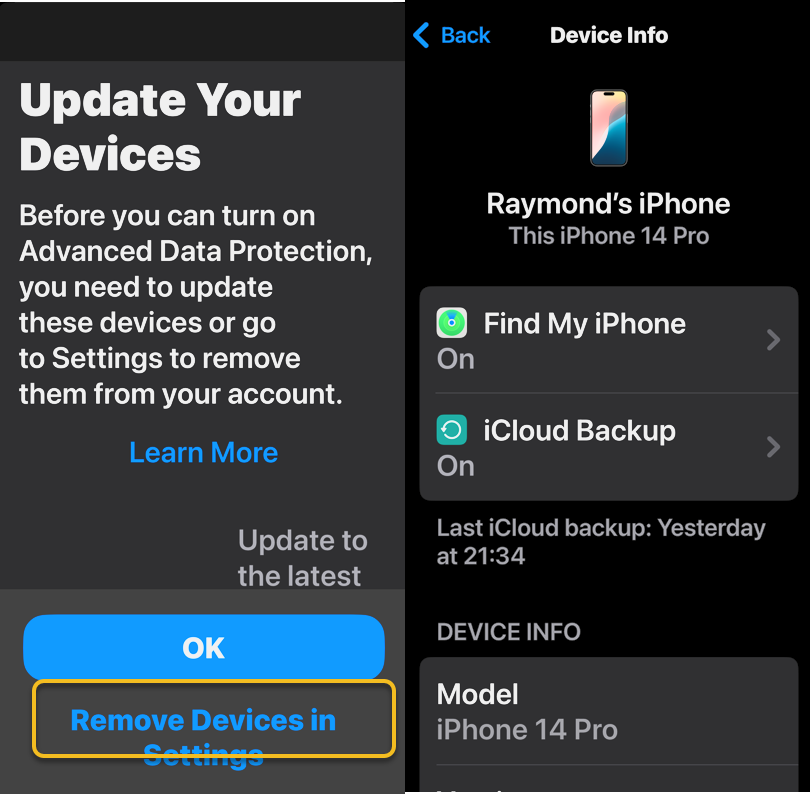
- If any of your devices do not qualify, you will be warned during the ADP setup process. If any of those are too old or you no longer have access to them, head to:
- Settings > Remove Devices and delete them from your list.
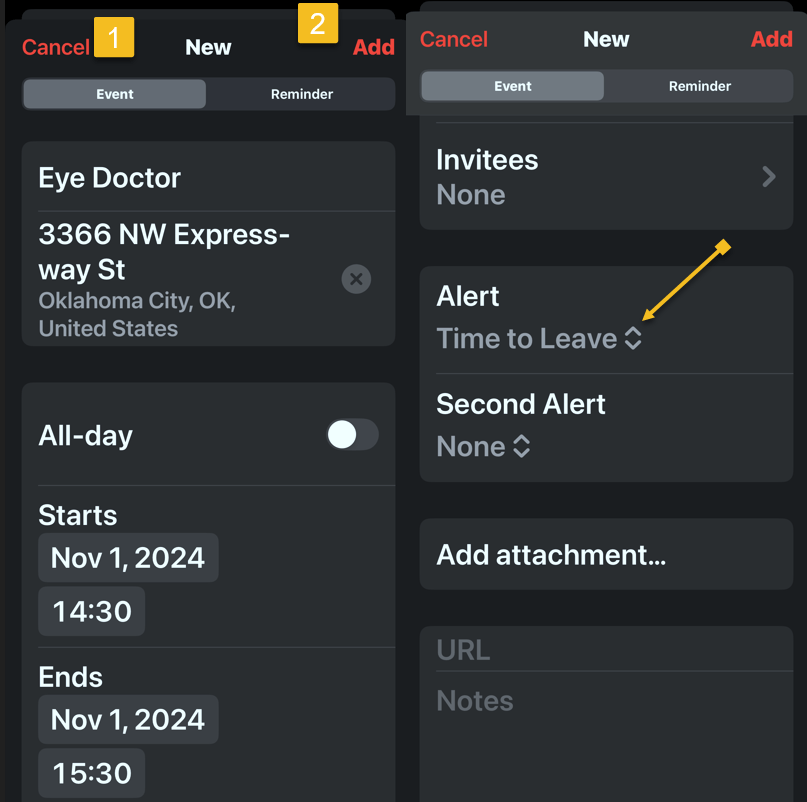
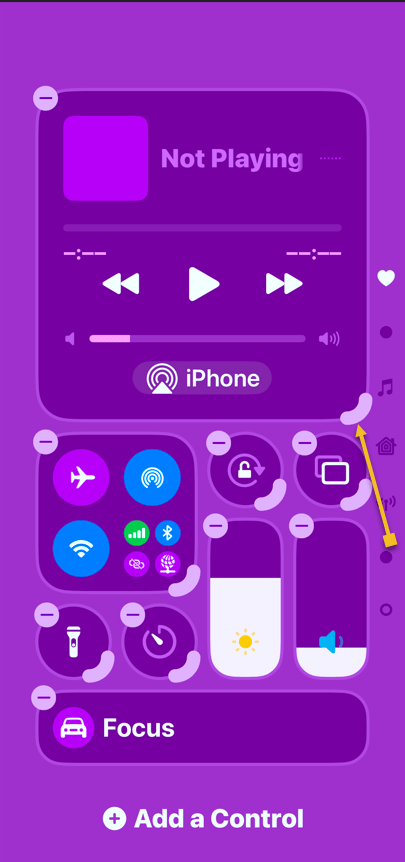
Refer to the below image:
How to Setup
To turn on ADP on an iPhone, iPad or Mac do the following:
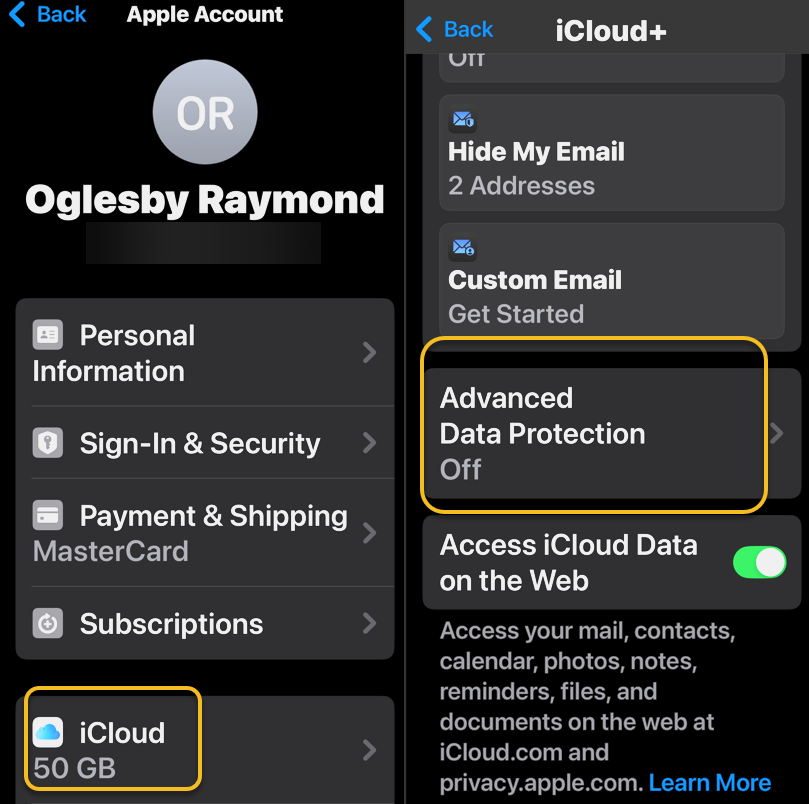
1. Go to Settings > [Your Name] > iCloud. On a Mac, open System Settings > [Your Name] > iCloud.
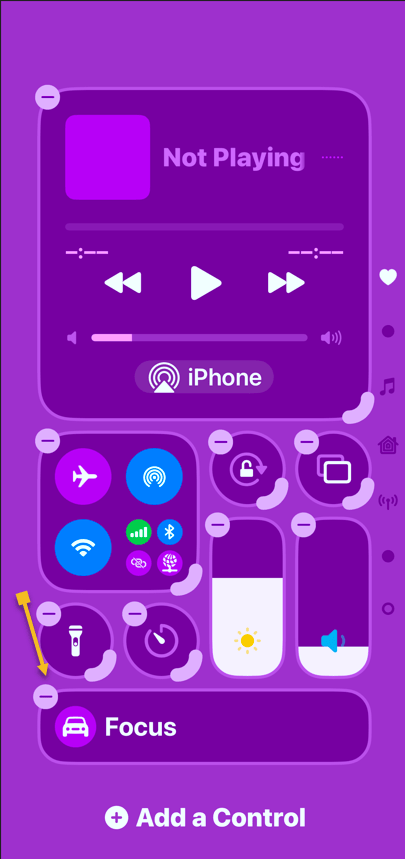
2. Scroll down to Advanced Data Protection, which likely says Off, and tap that to enable. This will take some time, and the screen will appear to be unresponsive; Just be patient. Later, if you want to disable ADP, repeat the above steps and select the Turn Off button.
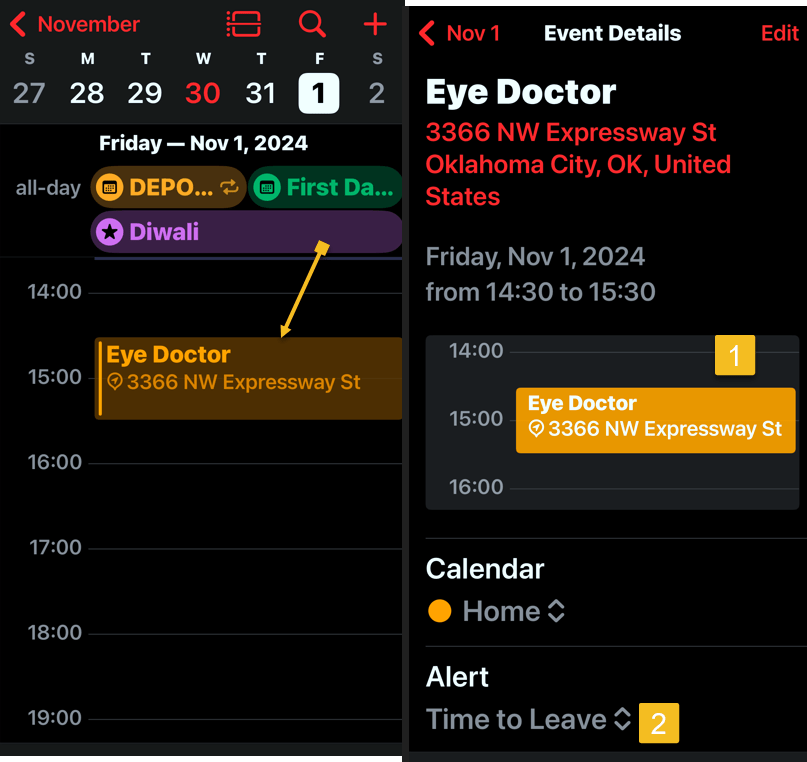
See the below image:
3, If there are any of the aforementioned impediments to setting up ADP, such as needing to update other devices on your account, you will review them on the next screen.
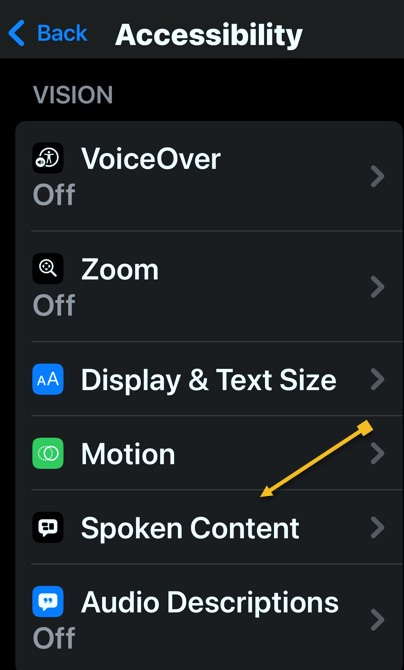
4. In the following screen, tap Review Recovery Options. You need to have a Recovery Key, Recovery Contact or both to ensure that you can get your data if you lose access to your iCloud account.
5. Enter your device’s passcode to finish.
See the following image:
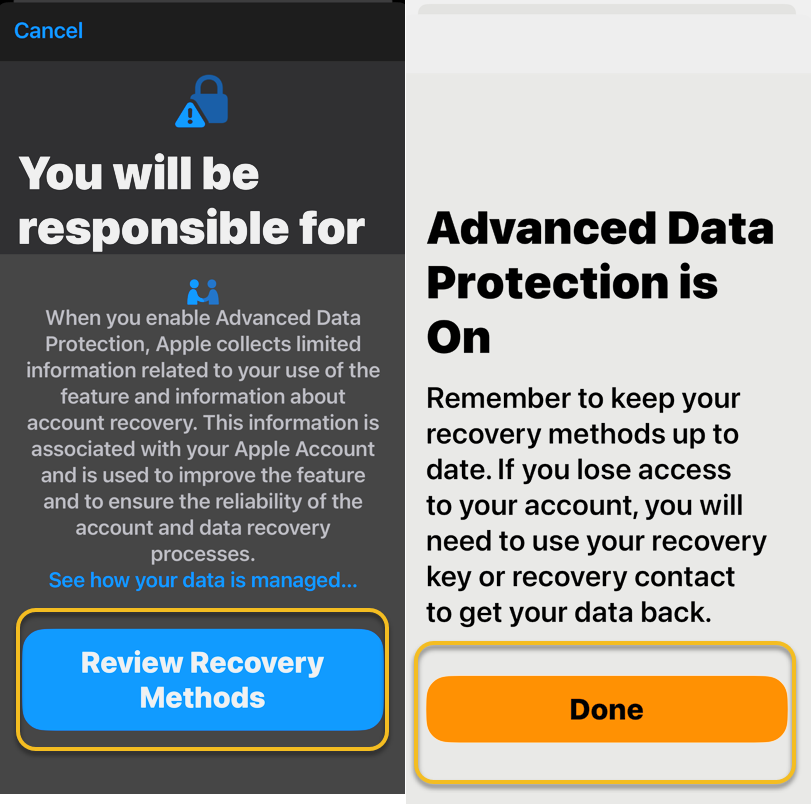
Activating ADP on one device means it’s on for all of your devices using the same Apple account, so you only need to set it up once.
Disclaimer
Technology is constantly evolving, and smartphone and desktop tech rarely remains static. Therefore, the information in this post is only accurate as of the date it was written. Blog posts that are older than six months may contain instructions that are no longer compatible with your device or operating system. We hope that the content from previous posts continues to function as intended. Thank you for reading TechSavvy.Life, where technology works for you.
Quote For the Day
. “Imagination is more important than knowledge. For knowledge is limited, whereas imagination embraces the entire world, stimulating progress, giving birth to evolution.”
-Albert Einstein
X (Twitter) info
That’s it. Please feel free to share this post! One way to share is via Twitter.
Just click the Tweet icon below. This will launch Twitter where you click its icon to post the Tweet.
Checkout TechSavvy.Life for blog posts on smartphones, PCs, and Macs! You may email us at contact@techsavvy.life for comments or questions.
Tweet
I Would Like to Hear From You
We value your feedback! Was this post helpful? Please share your comments with us. If you have a tech question related to your computer or smart device, feel free to reach out. Just send an email to contact@techsavvy.life, and be sure to include the device, app, and version you are using. To assist us further, you can also attach screenshots related to your inquiry.
The author’s Vietnam eBook on the “Battle for Tra Bong Vietnam: Events and Aftermath” can be accessed from a Kindle device or the Kindle App for a desktop or smartphone. The apps are free.